Hello folks to the first post of the Software engineer's security essentials series, in this series we will start from basic cybersecurity concepts, that each software engineer should be aware of, go all the way to the top risks and how to protect your business from them. This first post will serve as an introduction for basic concepts.
Part 1: Don't imitate, understand
Without Knowledge, the action is useless and knowledge without action is futile
The first step to having a good security reputation is Don't imitate, that means to face the problem, don't be afraid to search for problems in your system, it's a lot better that you find weaknesses in your system and fix them before bad guys do it, I've seen organization that refuses to invest in security and imitate they're safe, be aware You might be under attack and you don’t even know it
You should also understand, by understand I mean:
- understand cybersecurity concepts
- understand your current system
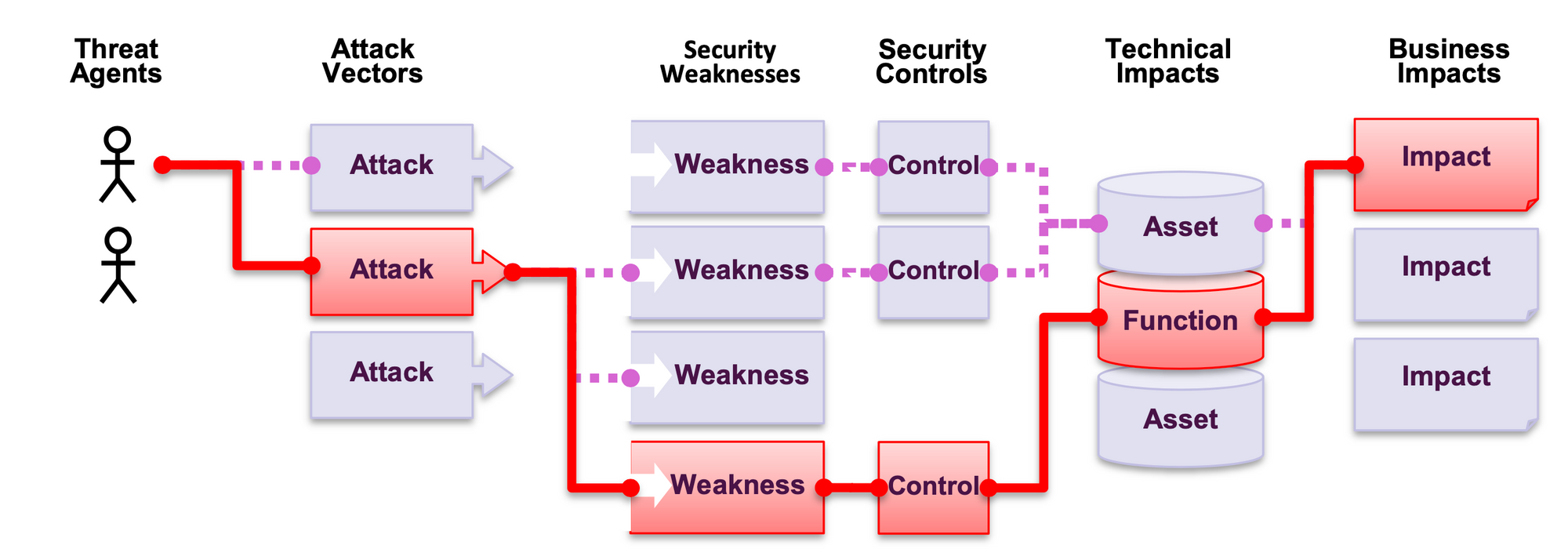
- understand threat agents, attack vectors, security weaknesses, and security controls
- understand technical impacts and business impacts
- understand your security risks
if you wanted to do the right action, you should have the right information
so, what is cybersecurity?
It is the protection of computer systems from malicious attacks or unauthorized access. This includes processes and preventative actions
Cybersecurity is much more than a matter of IT, it includes processes and preventative actions
If you think technology can solve your security problems, then you don’t understand the problems and you don’t understand the technology
but, why do we care?
In the age of IoT and AI, everything runs on computers, starting from your personal devices (smart device, car, refrigerator, cooling system, ..), going up to health systems and governmental systems. saying that, what if bad guys got access to your personal devices or worst what if they got access to governmental systems? what about data breaches
It takes 20 years to build a reputation and few minutes of cyber-incident to ruin it
There’s no silver bullet solution with cybersecurity, a layered defense is the only viable defense
what are security risks?
Risk is a path that an attacker can use to harm your business. Risk has to be assessed and scored to mark its importance. for example, some risks are trivial to find and exploit, and sometimes they are extremely difficult. Similarly, the harm that is caused may be of no consequence, or it may put you out of business. To determine the risk to your organization, you can evaluate the likelihood associated with each threat agent, attack vector, and security weakness and combine it with an estimate of the technical and business impact to your organization. Together, these factors determine your overall risk.
Elements of cybersecurity
There are four major parts of the cybersecurity system
- Information Security
- Network Security
- End-user Education
- Application Security
Information Security
This relates to preventing unauthorized access to information, with main principles called CIA - Confidentiality, Integrity, Availability
- Confidentiality: information should be private and accessed only by authorized parties.
- Integrity: information should be protected from changing or tampering
- Availability: information and resources should be available for authorized users
Network Security
This Includes practices and rules to protect unauthorized access to the underlying network, this can include hardware and software tools, this can serve as a great security control to limit incidents' effect
Measures to be considered
- Virtual Private Network (VPN)
- Network Access Control (NAC)
- Firewall Rules
End-user Education (cybersecurity awareness)
Amateurs hack systems, professionals hack people
You are the most important factor
They are the employees who use the hardware and software to do their job. starting from a software engineer, dev ops, operations, customer support, HR, ...., CEO.
Humans are the weakest link in a security system, you should take immediate actions to enhance end-user education, here are some preventive actions
- Security policies and protocols must be applied and respected.
- Security awareness training is essential for everyone.
- People should be aware of phishing, scamming, social engineering, and other common attacks.
- organizational culture, respect human factor role, invest in people
Don't neglect the human factor, this has caused severe damage over history.
You can’t hold firewalls and intrusion detection systems accountable. You can only hold people accountable
Application Security
These are protective actions to defend your applications against common attacks that leverage vulnerabilities to gain access to protected resources.
This needs a lot of discussions, and it will be the topic for the next part of this series.
That's it for this part, feel free to leave feedback in the comments section, and stay tuned for part2: Build your arsenal.
References
- https://www.globallearningsystems.com/end-user-security-awareness-training/
- https://www.eurasiareview.com/04082019-cyber-security-beware-the-human-factor-analysis/
- https://github.com/OWASP/Top10/blob/master/2017/OWASP Top 10-2017 (en).pdf
- https://cyberthreatportal.com/elements-of-cybersecurity/
- https://phoenixnap.com/blog/famous-social-engineering-attacks
- https://www.varonis.com/blog/government-hacking-exploits/
- https://www.csoonline.com/article/2130877/the-biggest-data-breaches-of-the-21st-century.html

